 In 2019, thousands of criminal cases in Orange County, California, became at risk of being overturned, not because of a lack of evidence, but because of how the evidence was handled over a two-year period. Not one or two high-profile cases but thousands, potentially putting thousands of criminals back on the streets!
In 2019, thousands of criminal cases in Orange County, California, became at risk of being overturned, not because of a lack of evidence, but because of how the evidence was handled over a two-year period. Not one or two high-profile cases but thousands, potentially putting thousands of criminals back on the streets!
Similar risks can arise anywhere, at any time, if the chain-of-custody isn’t followed correctly.
When used properly, electronic chain-of-custody tools not only prevent evidence mishandling but safeguard your operations against other vulnerabilities, ensuring that justice is served with unwavering accuracy, reliability, and integrity.
This article highlights the challenges that can disrupt the chain-of-custody and examines how purpose-built electronic management tools can help you avoid breaks in the chain.
Chain-of Custody Holds the Case Together
Forensic professionals need no introduction to the chain-of-custody. It’s the documented authentication process that’s required whenever evidence moves between people or storage locations: the current custodian releases it and the person receiving it takes custody, and both document the exchange. Alternately, the current custodian transfers the evidence to a storage location and authenticates the transfer.
If this process breaks down at any point, an entire criminal case can be compromised — and we’ve all seen many cases harmed throughout the history of the justice system. Any piece of evidence that’s been unaccounted for at any time could conceivably be tampered with, altered, exchanged, damaged, or compromised in some other way.
As a result, the chain-of-custody can make or break a case. So it’s no surprise that maintaining the integrity and accountability of the evidence chain is a critical priority for legal and forensic professionals. Doing so requires them to overcome a wide variety of challenges in an environment where there’s no room to make mistakes.
 Are Electronic Evidence Tracking Systems the Answer?
Are Electronic Evidence Tracking Systems the Answer?
Although tracking the chain-of-custody electronically seems like a good thing, the chain can still break down when managed by a digital system. Rigorous, reliable systems and procedures must be in place to maintain the integrity of evidence throughout its lifecycle, and to overcome challenges like the following:
- Rigorous Authentication Requirements: Every transfer of custody requires meticulous authentication. This process can be time-consuming and prone to human error, especially under high-pressure conditions.
- Dependency on Technology for Compliance: Electronic chain-of-custody systems introduce concerns about system reliability, user errors, and cybersecurity threats.
- Complex Evidence Handling: The need for strict protocols when evidence moves between people or locations adds complexity and the potential for procedural breakdowns, which can compromise cases.
- Accountability and Access Control: Ensuring that only authorized individuals have access to evidence is crucial. Any lapse in access control can lead to questions about the integrity of the evidence and the case.
- Visibility and Transparency: While it’s beneficial to have a clear view of the current custodian and full custodial history, ensuring this level of transparency requires robust, fail-safe systems.
- Impact of Custody Errors: Any error in the chain-of-custody can have dire consequences, potentially leading to the dismissal of critical evidence — or even entire cases.
- Training and User Adoption: With such high stakes in maintaining an unbroken chain, ensuring that every user is adequately trained and comfortable with the system is crucial.
- Integration with Existing Systems: Any evidence tracking system must integrate seamlessly with other systems in use from the crime scene to the crimes lab and beyond, ensuring that data is consistent, and the chain-of-custody is maintained without gaps.
- Evidence Lifecycle Management: Ensuring that the examiner has custody of the evidence to perform certain actions requires sophisticated business logic and system controls to prevent unauthorized actions.
Taking the Pain Out of the Chain for Investigators and Legal Teams
LabVantage Forensic Navigator is purpose-built for the forensic industry and provides a rigorous electronic chain-of-custody. This system goes far beyond the simple “check in” and “check out” functions of non-industry specific laboratory information management systems (LIMS) by building business logic around chain-of-custody. This system provides electronic authentication and documentation for transfers between people as well as to and from storage locations.
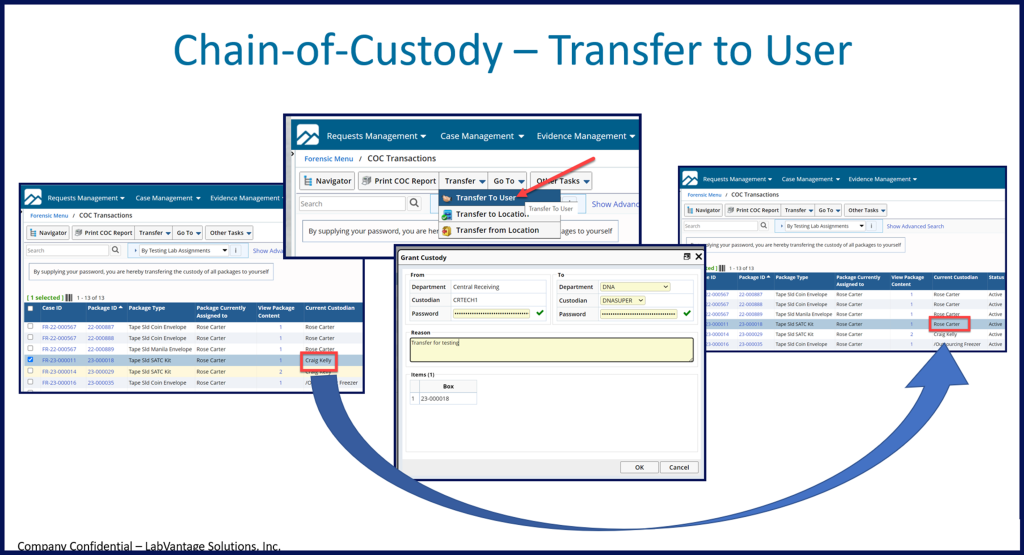
Transfers between users, for example, require both the releasing custodian and the person receiving the evidence to enter their username and password. Authentication can be performed by a single person if the evidence is being transferred to a storage location, but accountability is maintained in the same way.
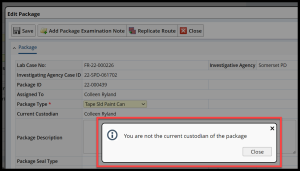
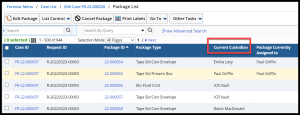
The integrity of the chain is rigidly enforced by business logic throughout the lifecycle of the evidentiary process. For example, the examiner must be the current custodian of the evidence to perform certain actions, such as adding package examination notes. The current custodian of any piece of evidence, and its full custodial history, can easily be viewed by authorized users at any time.
Forge a Stronger Link in Your Chain-of-Custody
LabVantage Forensic Navigator is more than just a tracking tool to help your organization maintain an unbroken chain-of-custody. It’s an ideal way to help you achieve true digitalization, becoming paperless from the crime scene to the courtroom. Request a demo today.



